Welcome to the Trezor Start Guide — your clear, human-first walkthrough for getting a hardware wallet up and running quickly and securely. This page focuses on practical steps and good habits: unboxing, initializing, creating a safe backup, connecting to apps, and avoiding common mistakes. Use this guide while you have your device nearby; follow each step deliberately and keep recovery information private.
Unboxing and first checks
Open the package on a clean, well-lit surface. Confirm the holographic seal is intact and inspect the device for visible damage. Trezor devices include a sticker or tamper-evident seal — do not use the wallet if the seal looks tampered with. Inside you should find the device, a USB cable, recovery seed cards, and a quick-start leaflet. Keep packaging until setup finishes successfully.
Initialize your device
Plug the device into your computer and navigate to trezor.io/start. The official web flow will detect your model and offer firmware updates. Only install firmware downloaded directly through the Trezor Suite or the official start page; unofficial downloads risk compromise. Follow on-device prompts — the device screen is the ultimate source of truth for confirmations, so always verify transaction details on the hardware screen, never solely in the browser.
Create a strong PIN
The device will ask you to create a PIN. Choose a PIN you can remember — long and random is best — and avoid obvious patterns like repeating digits or birthdays. The Trezor PIN protects the device if it is physically stolen. Do not store the PIN alongside the device or in a digital note.
Write down the recovery seed
Trezor displays a recovery seed phrase of 12, 18, or 24 words during setup. Write the words in order, exactly as shown, on the supplied recovery card or another durable medium. Never take a photo or save the seed digitally. Treat the seed as the ultimate key to your funds: anyone with those words can recover your wallet. Consider splitting the seed between secure locations or using a metal backup plate for long-term resilience against fire and water.
Verify your backup
After writing your seed, the device will ask you to confirm selected words. This step ensures you recorded the seed correctly. Only proceed once the verification passes. After verification, hide the recovery card in a secure place like a safe or deposited vault. Think about redundancy: one backup in a secure home location and another in a safe deposit box, depending on your risk model.
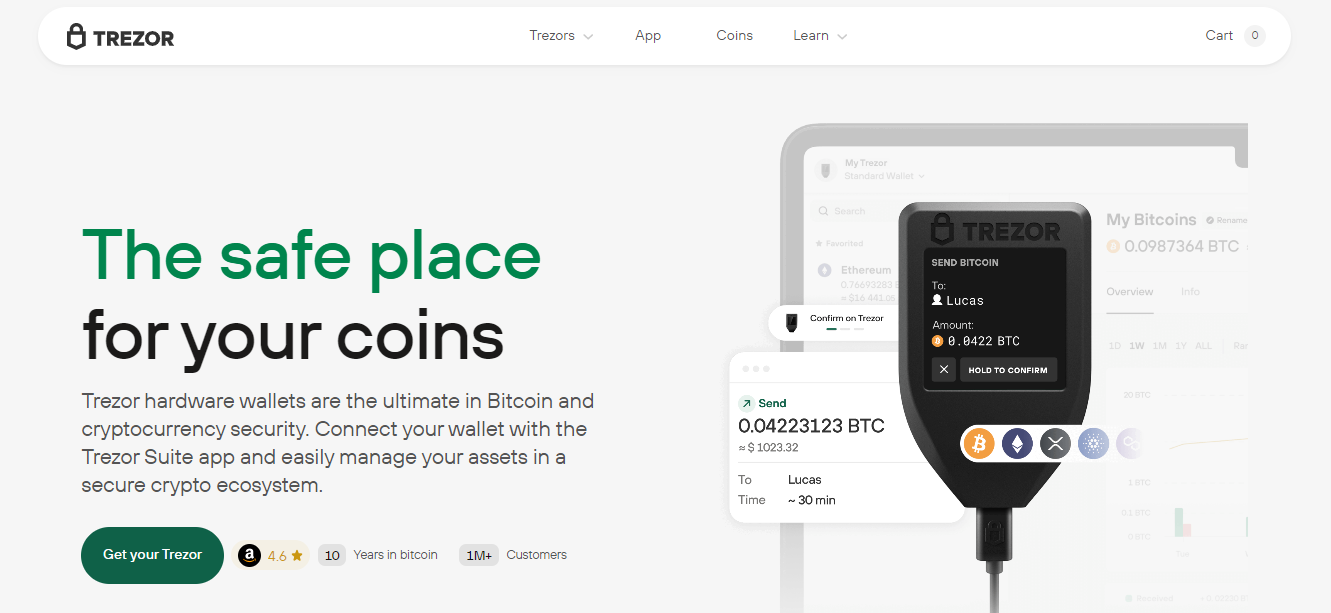
Install and use Trezor Suite
Download Trezor Suite from the official site to manage accounts, send and receive transactions, and check device health. Trezor Suite supports multiple cryptocurrencies and advanced features like coin control and transaction batching. Connect your device and allow the suite to enumerate accounts. For mobile use, follow the official instructions for Connect or Bridge; prioritize official apps to minimize attack surface.
Sending and receiving crypto safely
When receiving, always confirm the address on the hardware device screen before sharing it. When sending, double-check recipient addresses and transaction amounts on the device display. Enable advanced transaction options when you need specific fee control, but avoid making changes unless you understand them. For large transfers, send a small test transaction first.
Firmware updates and device hygiene
Keep firmware up to date — updates patch vulnerabilities and improve usability. Update only through the official interface and never accept firmware from unknown sources. If your device prompts unexpectedly while offline, disconnect it and re-check the official website for announcements. Secure your computer with up-to-date antivirus and a minimal set of browser extensions; untrusted extensions can expose sensitive information.
Advanced options: passphrases and hidden wallets
Trezor supports an optional passphrase that augments the recovery seed to create a distinct hidden wallet. This feature adds plausible deniability and extra security but increases complexity: if you lose the passphrase, funds in that hidden wallet are irretrievable. Use passphrases only if you fully understand the trade-offs, and treat the passphrase like a separate secret — never store it digitally.
Layered security practices
Combine hardware with good operational security: use unique passwords for exchange accounts and enable two-factor authentication (2FA). Prefer hardware security keys for accounts that support them. Avoid reusing recovery words, PINs, or passphrases across different wallets. Keep a written inventory of where you stored backups and who, if anyone, is authorized to access them.
Troubleshooting common issues
If the device is not recognized by your computer, try a different USB port, cable, or another machine. Check that the Trezor Bridge or Suite is installed and allowed by your operating system. If a firmware update fails, follow on-screen guidance precisely; contacting official support is safer than relying on third-party fixes. Never share your recovery seed on support channels.
What to do if your device is lost or stolen
If you lose possession of the device, you are still protected provided your seed and PIN remain secret. Immediately move any funds you can to a new wallet you control using the recovery seed on a new device. Consider moving funds to smaller, diversified addresses to minimize single-point risk. If you suspect your seed is compromised, act quickly and transfer funds to a fresh wallet.
- Confirm firmware is up to date.
- Test sending a small amount to verify workflow.
- Store the recovery seed offline and in multiple secure locations.
- Review connected apps and revoke unused permissions.
- Consider a metal backup for long-term durability.
Closing thought: Hardware wallets like Trezor significantly raise the bar for security, but they are not a substitute for careful operational choices. Protect your recovery seed, use strong PINs and passphrases thoughtfully, and prefer official software channels. With these practices, your Trezor becomes a durable fortress for your digital assets. Safe travels on the cryptographic frontier — keep your keys close and your practices cautious.